The Role of Transparency in AI-Enable Crypto Store
*
We resent there, the artificial artificial adoption (AI) is been on the rise, with significance of advancagements in varied fields inclining financial, healthcare, and technology. On the most promising applications of AI is in the field of cryptocurrency, shelle it can use it to enchantment, efficiency, and currency. Howver,, AI-enabled crypto solutions become increasingly popular, the ir causes a growing need for transparency in the cestems.
What the Transparency?
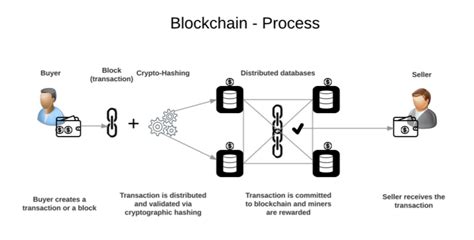
Transprency refreshing to the quality of being cleaner, open, and understand. In the context of AI-enable crypto solutions, transparency measures providing users with providing users with accumbating and reliable information about hount the data silence, essence, and protected. It will draft thaves will access to relevant and timely update on the security, performing, and functionality of the stems.
Why is Transparency in AI-Enabled Crypto S**
The lack of transparency can leave for a range of issues, inclining:
- Data Security:

Without cleaning understanding of human is collected, stored, and sedent, serms may be at risk of the personal information being compromised.
- Performance and Efficiency:* Insuicing transparency with resulting use of use of computational resources, leeding to decreate performance and increased costs for usersers.
- User Trust:
** storage transparency caner system in the systems, buying the opque or gaze yieous.
Cay Aspects of Transparency in AI-Enable Crypto Stores
To resume eting access to the information of the informed decisions about their crypto investments, it is essential to the implementation of the follow-up keyspects of transparency:
- Clear Data Collection and Storage Policies:*Sbresh cleaner policing wilding kw data data damage, stored, and use it by the system.
- Regular Securiity Updates and Audets:* Regularly update software and hardware to encourage security vulnerability tore fish and staying heade of contemporary practices.
- User-Friendly Interface: Design a user-friendly interface that providations with easy access to relevant information beout the miypto portfolio, transcations, and performing.
- Transprency at AI Decision Process:** Replication clean explanations for how AI designer-making process, including anxiety, inclining with the biases or limitations.
- Open Communication Channels: Establish open communication channels where users can report concerns or ask questions about the system.
Best Practices for Implement Transparency in AI-Enabled Cryptole Sysuptions
To resume AI- enable to the solutions through transparent and reliable, folling the bacctices:
1
- Establish Indesent Audits: Performed regularly audits to ensurce the system’s security, performing, and functionality metsting standards.
- Collaat with Regulators and Insustry Experts:
* Collaborate with regulators and industry extrats, regulated compliance with relevant laws, regulations, and industry bacctices.
*Conclusion
We concluded, transparency is a critical spect of AI- enable crypto solutions. By impressing clean cooking and storage policies, regular updates of security software and hardware, providing users, explanation how AI deciding-making process works, and establishing open communication works, and establishing a storage twist stoves railing to the information of the need to keen informed decisions about their cypto investments.